What is Wharf?
Wharf is a cloud-native and progressive security layer designed to safeguard your data services in any environment, at any scale.
It follows an API-first design and the principle of least privilege to prevent unauthorized accesses to your sensitive data.
Components
The security layer is based on a lightweight binary — a protocol-aware service proxy — that you can deploy as a sidecar container alongside your services or as a standalone reverse-proxy in high-availability mode. The second component is a control plane that allows you to manage your Wharf resources such as your policies or your identities.
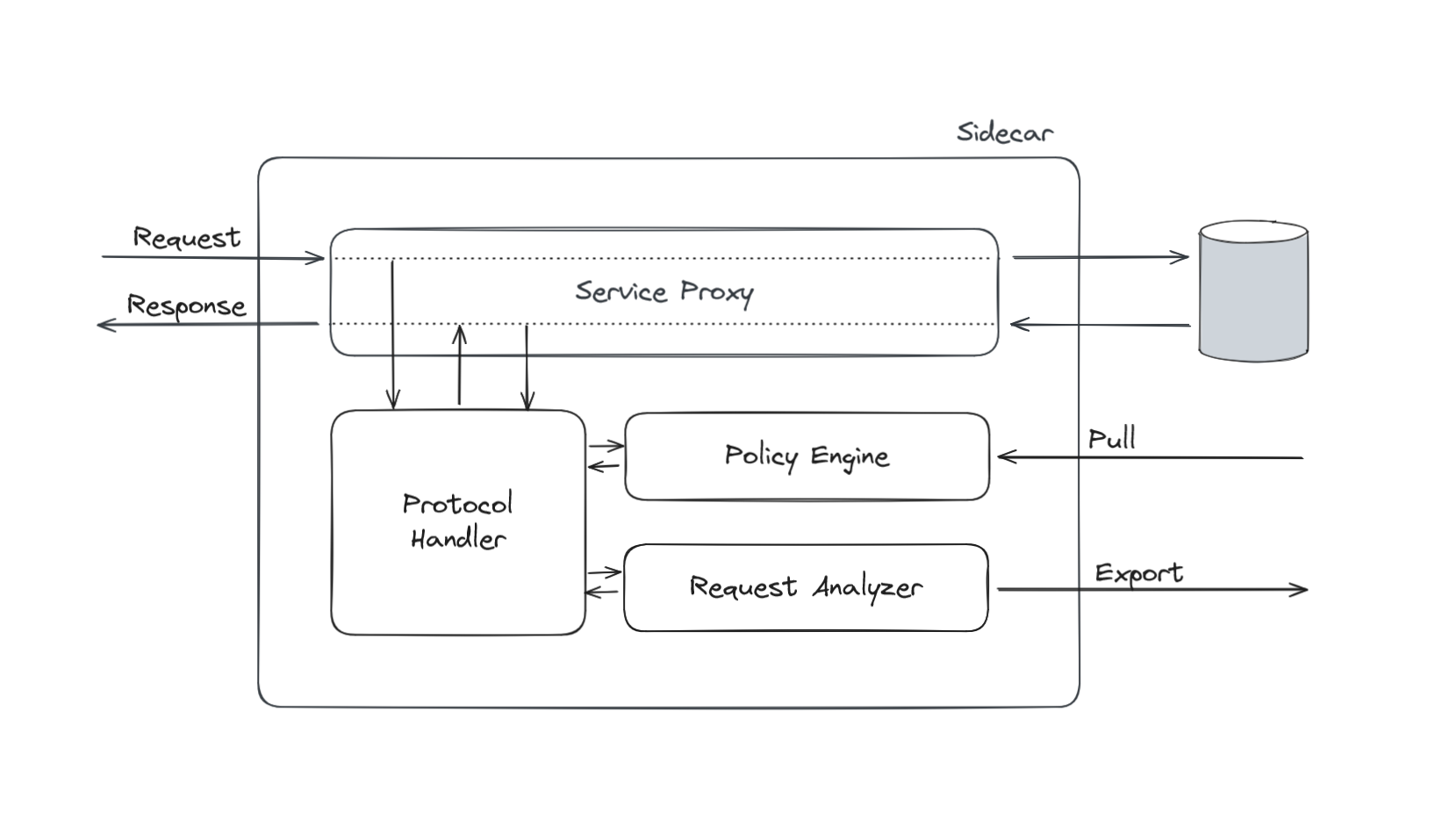
Sidecars
Wharf protocol-aware service proxies, or Wharf sidecars, are deployed close to their data source to avoid latency. In proxy-mode, the multiple sidecars have their own URLs, and the protected service is still accessible from the internal network. In sidecar-mode, the single sidecar associated with the protected service (or replica) is able to substitute the original address with its own address, thus restricting direct access to the service even from the internal network. The sidecars' functionnalities range from low-latency access decision to asynchronous field masking, through passive indexation and access logs export.
Control plane
The control plane allows you to manage your sidecars' lifecycle, your access control policies, your data consumer identities, and to retrieve your auto-discovered data inventories or your sidecars' access logs. You can interact with the control plane through a web platform, an API or with Infrastructure-as-Code.
Features
Wharf security layer is built around a set of four features, that you can use in a standalone manner or all at the same time.
Dynamic inventory discovery
When a sidecar is healthy, it continuously discovers its associated data source(s) to populate complete and updated inventories.
- Add metadata or tags to specific fields or resources for classification.
- For structured data, built-in row-level introspection at regular intervals.
- For undocumented or unstructured data, passive indexation at request runtime.
Access control decision
A sidecar interacts with an authorizer for making access decisions. The authorizers are managed by the control plane, and they are scaled horizontally or vertically to meet complex scenarios, such as a low-latency constraint on a large permission set. A sidecar can be synchronized with an authorizer to achieve zero-latency access decision.
- Policy-as-code with Rego, an open-source policy language.
- Granular access control decision (field-level, row-level).
- Support for RBAC, ABAC and ReBAC models.
Asynchronous data masking
Sidecars are able to mask sensitive data asynchronously. When a read-request is sent to a sidecar, its structure is immediately analyzed to detect and then pre-mask fields which contain sensitive information as PII, PHI or PCI.
- Asynchronous field masking for read-requests.
- Built-in and custom rules for named entity recognition.
- Customizable for other text or image masking.
Access logs and metrics
The sidecars log every request to their associated data source(s).
- Access logs monitoring for real-time threat detection and audit reports.
- Prevent shadow accesses and potential data breach.
Use cases
Wharf aims to help data and security engineers solve privacy issues related to their databases, data warehouses, APIs, RAG pipelines or even LLM applications, in a quickly manner.
Sensitive data encryption
The security layer allows detecting, filtering, and masking sensitive data found in a request. For example, if a request to an API contains a field named "email", the named recognition module will automatically identify and encrypt this field. Another example, if a request - or a response - from an LLM-prompt contains critical data related to your business, you can customize the module and import your own logic to mask privacy leaks in your prompt inputs and outputs.
Access control management
The security layer provides an authorizer compatible with Rego, an open-source policy language, designed for stateful attribute-based access control. For example, you can restrict user access to a resource depending on its location or its current device, or any other attribute. Thanks to built-in libraries, you can use Rego for RBAC, ABAC, and ReBAC models, depending on your scalability requirements.
Auditing and compliance
The security layer is also a full-featured observability layer, allowing an organization to restrict shadow or unauthorized accesses to their data sources, reducing the risk of data breach or data theft. You can detect unusual behaviors or potential threats in real-time thanks to configurable alerts and generate audit reports to prove your compliance.
Deployment models
Wharf offers flexible deployment options to meet your organization's needs.
Cloud managed
Use Wharf as a cloud managed solution, allowing you to leverage the benefits of cloud infrastructure without the hassle of managing your own servers. With Wharf's cloud managed option, you can easily scale your data security layer as your organization grows.
Platform as a Service
Opt for Wharf's Platform as a Service (PaaS) deployment model, giving you the ability to use a cloud managed control plane and to deploy self-hosted sidecars in your own infrastructure with a shared responsibility model.
On-premise plan
Deploy Wharf's on-premise for complete control over your security layer and control plane. With the on-premise deployment option, you have the flexibility to deploy Wharf on your own infrastructure, ensuring data remains within your organization's network.
Please contact us for any information, required features, integration support.